Emergency: 3 CVE-2025-20333 Threats That Will Destroy Your Network Security in 2025
When you searched for ‘CVE-2025-20333’ at midnight, you weren’t looking for another routine security bulletin—you needed immediate answers about CISA’s Emergency Directive 25-03. Meet Sarah, a network administrator who discovered her Cisco ASA firewall was under active attack by nation-state actors just 48 hours ago…
The Bottom Line: What September 2025 Data Reveals About CVE-2025-20333
CISA issued Emergency Directive 25-03 on September 25, 2025, mandating immediate patching of CVE-2025-20333 and CVE-2025-20362 vulnerabilities in Cisco ASA and Firepower devices. The threat is active right now—CVE-2025-20333 carries a CVSS score of 9.9 and enables attackers to execute arbitrary code as root on your firewall.
The Avoidance Path: When organizations ignored emergency patching protocols, threat actors gained unauthenticated remote code execution and manipulated read-only memory (ROM) to persist through reboots and system upgrades. Your firewall becomes their permanent backdoor.
How CVE-2025-20333 Actually Impacts Your World in September 2025
This isn’t just another vulnerability bulletin—it’s a nation-state warfare scenario unfolding in real-time. Cisco disclosed four zero-days, including three targeted by the same threat actor behind the “ArcaneDoor” campaign. The attackers aren’t just breaking in; they’re rewriting your firewall’s firmware to survive complete system rebuilds.
CVE-2025-20333 exploits improper validation of user-supplied input in HTTP requests, allowing attackers with valid VPN credentials to send crafted requests. But here’s the terrifying part: when chained with CVE-2025-20362, attackers gain completely unauthenticated remote control.
Your Cisco ASA devices aren’t just compromised—they become weaponized infrastructure for further attacks against your organization and others.
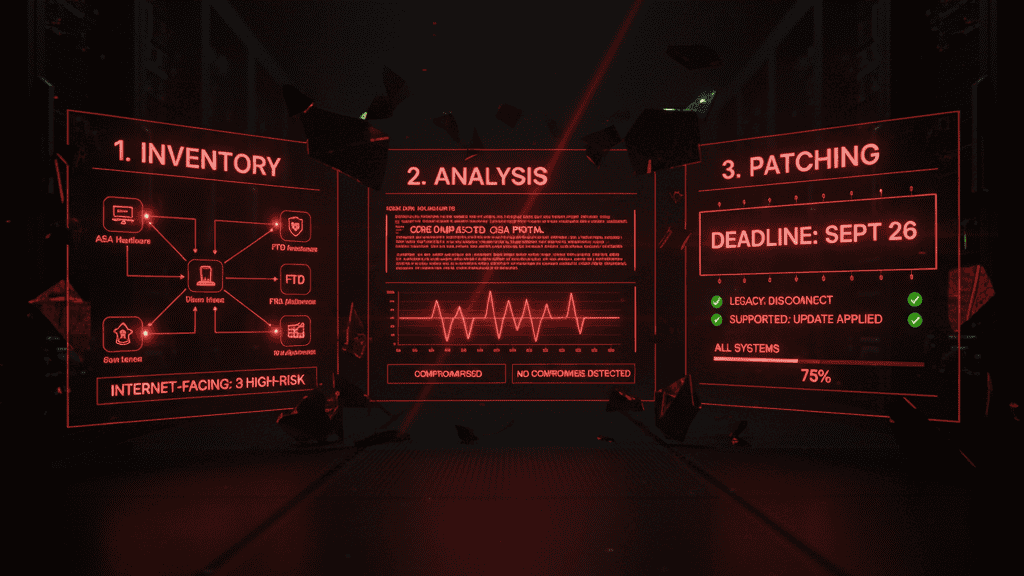
Your 3-Step Emergency Action Plan: Mastering CVE-2025-20333 Response
1. CVE-2025-20333 Device Inventory: Immediate Identification Protocol
Deadline: NOW – Identify every Cisco ASA platform in your environment:
- ASA hardware appliances
- ASA Service Modules (ASA-SM)
- ASA Virtual (ASAv) instances
- ASA firmware on Firepower 2100/4100/9300 series
- All Cisco Firepower Threat Defense (FTD) appliances
Critical Action: Document which devices face the internet—these are your highest risk targets.
2. Forensic Analysis Implementation: Core Dump Collection
Deadline: 11:59 PM EDT September 26, 2025 for public-facing devices:
- Follow CISA’s Core Dump and Hunt Instructions and submit core dumps via the Malware Next Gen portal
- If “Compromise Detected”: Immediately disconnect (don’t power off) and report to CISA
- If “No Compromise Detected”: Proceed to patching requirements
3. Emergency Patching Optimization: Version-Specific Actions
Deadline: 11:59 PM EDT September 26, 2025:
- Devices with end-of-support dates on or before September 30, 2025, must be permanently disconnected
- Supported devices must download and apply latest Cisco updates, then apply all subsequent updates within 48 hours of release
Frequently Asked Questions About CVE-2025-20333
What makes CVE-2025-20333 different from other Cisco vulnerabilities?
This vulnerability allows threat actors to manipulate ROM memory, persisting through reboots and system upgrades. Unlike traditional attacks that lose access after restarts, this creates permanent backdoors that survive complete system rebuilds.
Sarah’s Two-Path Discovery: The 3 Critical Decisions
The Advantage Path: When Sarah’s team followed CISA’s emergency protocol within 6 hours of the directive…
- Rapid Device Inventory: Discovered 12 Cisco ASA devices, including 3 internet-facing appliances that required immediate forensic analysis
- Proactive Core Dump Analysis: CISA’s analysis revealed “No Compromise Detected” on their devices, enabling continued operation after patching
- Strategic Patch Management: Successfully updated all supported devices and identified 2 legacy appliances for immediate replacement
How do I know if my Cisco ASA device is already compromised by CVE-2025-20333?
CISA requires core dump collection and analysis for all public-facing ASA hardware appliances using their specific forensic procedures. The analysis will definitively indicate “Compromise Detected” or “No Compromise Detected” status.
What’s the connection between CVE-2025-20333 and the ArcaneDoor campaign?
Cisco assesses this campaign is connected to ArcaneDoor activity from early 2024, with the threat actor demonstrating capability to modify ASA ROM since at least 2024. This represents an escalation of an ongoing nation-state operation.
The Verdict: Why CVE-2025-20333 Matters More in September 2025
Sarah’s team avoided becoming another statistic in nation-state cyber warfare because they treated this as what it is: an active battlefield scenario, not routine maintenance. CISA’s February 1, 2026 deadline for comprehensive reporting shows this threat campaign will continue evolving.
Your firewall isn’t just infrastructure anymore—it’s either your strongest defense or your biggest vulnerability. The choice is yours, but you have less than 24 hours to make it.
Essential Resource: For complete technical guidance, review CISA’s official Emergency Directive 25-03 documentation.
To read more news about AI click here