The F5 Networks compromise has rapidly become one of the most critical cybersecurity incidents of 2025, with severe implications for enterprises and infrastructure worldwide. The breach, attributed to a highly sophisticated nation-state threat actor, resulted in the exfiltration of F5 BIG-IP source code and internal vulnerability research, creating an immediate risk of widespread zero-day exploitation across exposed systems.
For organizations that depend on F5 BIG-IP for traffic management, security, or application delivery, understanding the scope and urgency of this incident is essential.
What Happened in the F5 Networks Compromise
According to F5’s official investigation, the attacker maintained long-term unauthorized access to certain internal environments before being discovered in August 2025. While customer databases and billing systems were not accessed, the intruders successfully exfiltrated:
- BIG-IP source code
- Engineering documentation
- Internal vulnerability information
- Configuration and implementation details for some customer environments
Although there is currently no evidence of source-code tampering, the stolen data enables attackers to discover flaws much faster than through traditional black-box testing — significantly increasing the probability of real-world exploitation.
Why the F5 Data Exfiltration Is So Serious
BIG-IP devices play a direct role at the edge of enterprise networks, making them high-value targets. The stolen information gives attackers a strategic advantage, enabling:
- Rapid development of zero-day exploits
- Targeted intrusions against specific customers using leaked configuration data
- Credential theft and lateral movement
- Long-term persistence inside high-value environments
- Potential supply-chain attack paths
More than 266,000 BIG-IP instances are exposed to the internet, increasing the global attack surface dramatically.
Who Is at Risk
The impact of the F5 Networks compromise spans across sectors, especially:
- Government and public sector networks
- Telecom and ISPs
- Banking and financial services
- Healthcare systems
- Energy and critical infrastructure
- Large-scale enterprise cloud deployments
Any organization running unpatched BIG-IP systems is at immediate risk — even if the management interface is not publicly exposed.
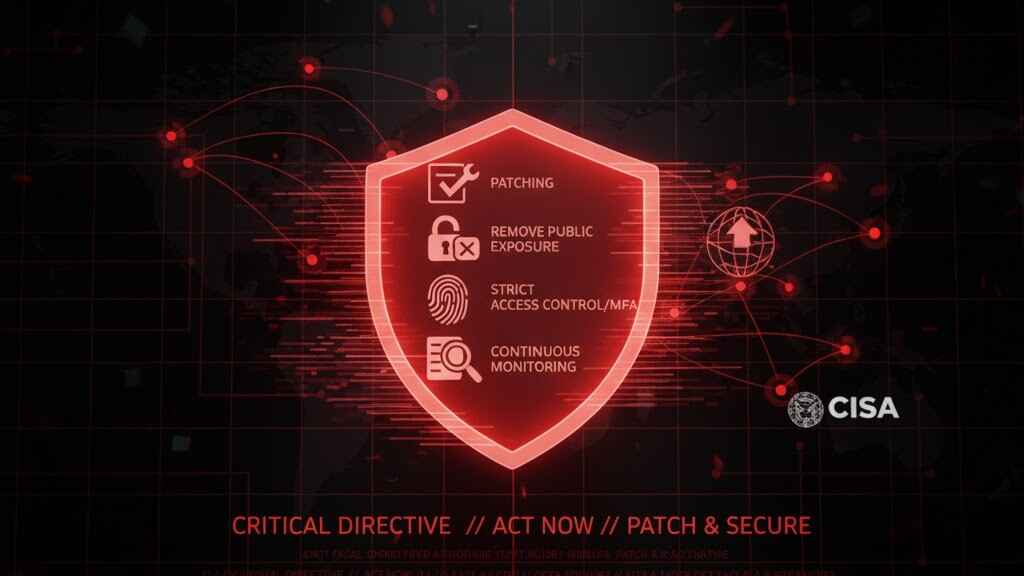
Emergency Mitigation Steps (Must-Do Checklist)
To reduce the risk of exploitation following the F5 breach, organizations should act without delay:
1. Patch All BIG-IP Systems
Apply the latest security updates released by F5 across supported versions.
2. Remove Public Exposure of Management Interfaces
Do not allow public internet access to administrative portals.
3. implement Strict Access Control
Require MFA for administrative users; rotate credentials immediately.
4. Perform Threat Hunting
Request and apply F5 IOCs and analyze logs for suspicious lateral movement.
5. Validate Configuration Integrity
Check for unauthorized changes in iRules, WAF policies, network routing, and certificates.
6. Enhance Continuous Monitoring
Enable SIEM / SOAR alerting for anomalies involving F5 deployments.
Failure to take these actions creates a real risk of compromise even on fully patched systems if stolen configuration data is already in attacker hands.
CISA Advisory and Global Response
In response to the F5 Networks compromise, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive requiring public agencies to:
- Inventory all F5 assets
- Patch or remove vulnerable appliances
- Conduct compromise assessments
Private-sector cybersecurity firms also warn that attackers may stockpile exploits and deploy them gradually — meaning vigilance must continue well beyond initial patching.
Long-Term Lessons from the F5 Breach
This incident underscores critical realities in cybersecurity:
| Lesson | Why It Matters |
|---|---|
| Protecting source code is critical infrastructure | Code exposure accelerates exploit development |
| Network-edge appliances are high-value targets | They provide direct access to internal environments |
| Vulnerability knowledge is as valuable as credentials | It enables silent, stealthy compromise |
| Supply-chain risk must be treated as persistent | Manufacturers are now high-impact attack vectors |
Organizations should integrate these lessons into future procurement, vendor due diligence, and incident response planning.
Conclusion
The F5 Networks compromise is not just another breach — it is a global cybersecurity event with long-tail consequences. Because attackers now possess source code and vulnerability data, organizations must assume that future zero-day exploitation is inevitable and act defensively today rather than reactively tomorrow.
If your organization deploys F5 BIG-IP, the next 90 days are critical for strengthening visibility, patching, monitoring, and access control.
FAQs — F5 Networks Compromise
Is the F5 breach fully contained?
Containment efforts are ongoing. The stolen data cannot be retrieved, so risk remains long-term.
Was customer PII stolen?
F5 reports no access to customer billing, CRM, or financial systems.
Can patched systems still be attacked?
Yes. If stolen configuration data relates to a specific environment, attackers could perform targeted exploitation.
Should organizations replace rather than patch?
Replacement is not mandatory, but patching must be immediate. High-security environments should consider device segmentation and architectural redesign.
Is BIG-IP safe to use today?
Yes — if patched, hardened, and continuously monitored.
You can also read more about this subject from here
To read more news about technology click here
And to read more about AI click here